Security and trust
What data do you require access to ?
User accounts for use identification; CRM user contact details. CRM data for searching, display; accounts, contacts, leads, opportunities. Email/calendar items for display/copying and analysis. For full details please review our privacy policy.
Do you have privacy controls ?
Yes, we provide controls of what data is processed by Ebsta. Within Ebsta, we provide control over who gets visibility of data at a role based and team level.
Where is data stored ?
All data is stored in AWS (USA East). Ebsta has signed with Amazon the AWS Data Processing Addendum, which includes the Model Clauses.
Is data encrypted ?
Yes, all data is encrypted during transit and at rest.
Do you follow a standard approach to information security – ISO/SOC ?
Yes, Ebsta is ISO 27001 compliant.
What happens once I connect a service account ?
Once you connect a service account to Ebsta, we check that it has impersonation rights to the mailbox specified to validate configuration. No data is processed.
Once the service account is connected, the mailboxes you wish to process are then specified. The service account will validate that it has impersonation rights but nothing is processed until the admin user explicitly starts the sync on the selected mailboxes.
Once data is processing, please also note, that the service account configuration, the blacklisting, search rules, Ebsta privacy controls and user roles define what data is being processed and presented to the owner of the data.
Why should I use a service account ?
Service accounts allows admin management of connections to Ebsta, providing centralised controls for configuring, starting and stopping Ebsta services and central management of access that Ebsta has over your environments. Most of all service accounts generally come with a better SLA on service availability and also negate disconnection issues which occur when users passwords rotate.
What happens to our data once we leave ?
Upon leaving Ebsta, we destroy data processed on your behalf after 60 days. Full details in our Terms.
Who owns the data stored in Ebsta ?
Data that we process on your behalf is processed by a data processor and will give you full ownership of that data at all times.
Will you sell our data or analyse it for advertising purposes ?
No, we process data on your behalf. The data remains yours and we will never sell, share or use your data for anything other than providing the Ebsta services back to you.
What control do I have over my data ?
You retain control over your data at all times, you can revoke access to your systems at any time and control all privacy, search and blacklisting rules. Data can be removed upon request.
Do you support SSO ?
Yes, we will be able to use the identity provider you already use to access your CRM and communication systems.
Do you store my passwords ?
No, we use your CRM as our primary identity provider and only connect users to systems via OAuth, so we’ll never ask you for nor process your password.
Do you have 3rd party security reviews ?
We are subject to annual 3rd party security reviews by Salesforce as an ISV partner and the Google Cloud Platform as part of their OAuth reviews, as well as our own 3rd party reviews.
Ebsta Architecture
The Ebsta platform runs solely on the Amazon Web Service platform in a virtual private cloud, VPC.
With a layered approach to security and threats Ebsta uses services such as Amazon Elastic Load Balancers, Web Application Firewall, Inspector and follows Amazon’s best practice recommendations. Server access is restricted in private subnets with the configuration of both security (stateful firewall) and network ACL (stateless) for both inbound and outbound traffic. Servers are based on AWS Role security and are split by instance responsibility, communication between our instances internally and externally is transmitted end to using SSL.
Access to servers is via application and HTTPS via users with valid tokens, licences, access rights or via IP restricted VPN (Ebsta only) with MFA.
3rd party data sources (CRM and email providers) connections are managed at server level over SSL.
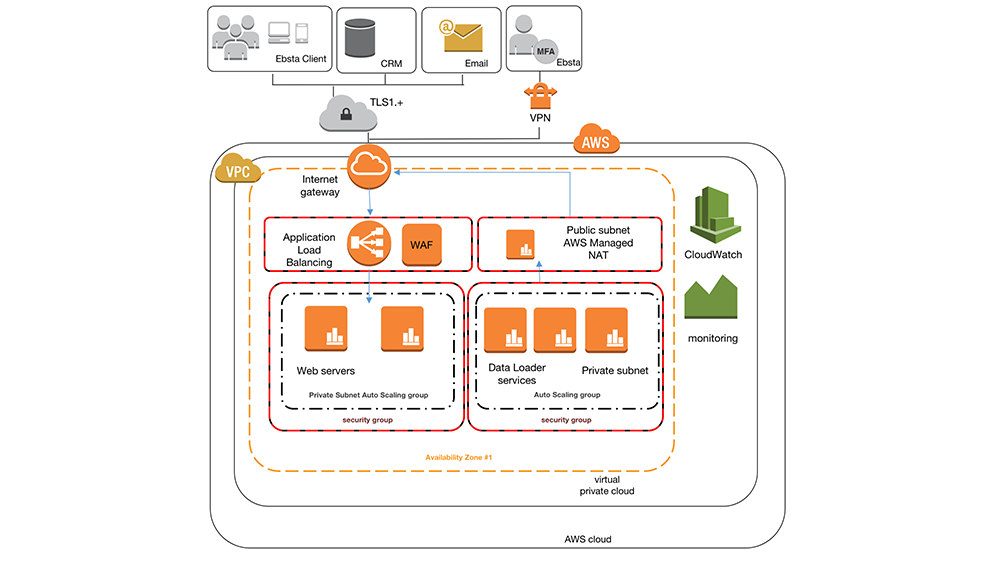
Hosting Environment
Currently to provide the most performant global solution the Ebsta platform utilises AWS US-East.
Ebsta has signed with Amazon the AWS Data Processing Addendum, which includes the Model Clauses.
Sub Processors
Where Ebsta Ltd acts as a data processor on behalf of the data controller the following sub processors are used to assist in delivering the Ebsta services.
- Amazon Web Services, Inc
Ebsta uses a commercially reasonable selection process to evaluate the security, privacy and confidentiality practices of sub processors and minimises sub processor use to a minimum.
Access Control
Users connect to Ebsta via OAuth using Salesforce as an OAuth provider. Initial connection facilitates Ebsta account (for details of information gathered see our privacy policy) creation, user assignment to org and licensing. Ebsta supports 2 roles, user and administrator. Ebsta administrator permissions are inferred from Salesforce permissions and can be subsequently provided by administrators to users.
All data is accessed in the context of the logged in user and record and field level security is maintained at all times.
Users/customers at all time are in control of assigned tokens and can revoke at any time.
Data Transmission and Storage
All communication with Ebsta occurs via TLS v1+ connections.
Data stored to deliver the features of the Ebsta Team and Enterprise editions is encrypted at rest. Each object is encrypted (AES-256) with a unique key employing strong multi-factor encryption. As an additional safeguard, it encrypts the key itself with a master key that regularly rotates. Through the use of AWS KMS all keys are held securely.
Data Access
Application initiated requests for data access pass through multiple application levels to validate that the user is authenticated, licenced and belongs to the customer associated with the data and has the permissions to view/edit as requested. Only upon all checks being successful is data returned.
Administrative access to the production environment is locked down to a few select senior employees via IP restricted VPN requiring multi factor authentication.
Logging & Monitoring
All application layers and processing transactions and system requests are logged and monitored. Infrastructure access is monitored by AWS Cloudwatch. Application performance is monitored by NewRelic. All monitoring systems implement thresholds that when exceeded notify internal personnel via multiple channels 24-7-365.
Incident Response & Disaster Recovery
The Ebsta platform is entirely cloud based. Core services are redundant across multiple data centres and we rely on the BC/DR capabilities of AWS.
In the case Ebsta determined that any customer information was compromised, Ebsta will immediately notify the customer primary contact and the relevant supervisory authority, if relevant, within 72 hours.
Application Development
Ebsta implements security consideration at design time and employs best practice secure coding principles (OWASP) with extensive employee training.
Ebsta runs multiple development, testing, staging environments which contain no client data. Transition of code between environments is subject to peer review and software based analysis before continuous integration. Application and source code is scanned by vulnerability detectors and we are subject to 3rd party security reviews and penetration testing.
Salesforce Security Approved
Ebsta are an official Salesforce ISV Partner. Ebsta has been through the strict security review process which is in place to evaluate the security of their partners to ensure that they are trusted to deliver and handle your valuable data in the same way that they do themselves.
https://developer.salesforce.com/page/Requirements_Checklist
Employees
Employees are vetted before employment and all sign up to acceptable usage and confidentiality agreements.
Issue Reporting
To report any security concern or suspected vulnerability please contact the Ebsta Security Team
Policies/Further information
Ebsta Privacy Policy – https://www.ebsta.com/privacy-policy/
Ebsta’s ISO 27001 Announcement – https://www.ebsta.com/ebsta/iso-27001-certified/
Ebsta Terms and Conditions – https://www.ebsta.com/terms/
AWS Compliance – https://aws.amazon.com/compliance/eu-data-protection/
AWS Best Practice – https://d0.awsstatic.com/whitepapers/AWS_Cloud_Best_Practices.pdf
AWS Security – https://aws.amazon.com/security/
Salesforce Partner Security – https://security.secure.force.com/security/partners
Salesforce Security Checklist – https://developer.salesforce.com/page/Requirements_Checklist
To find out more about how Ebsta can help your organisation, please get in touch.